When optimizing AWS cloud costs, networking charges often go under the radar. Most FinOps teams focus on EC2 right-sizing or S3 tiering — but ignore network egress, data transfer fees, and AZ routing behavior. The truth? A few simple networking choices can yield significant savings without compromising performance.
In this article, we’ll simplify AWS networking cost optimization by focusing on two actionable best practices:
-
- Prefer private IP traffic over public IP
-
- Use the same Availability Zone (AZ) when architecting communication between services
Understanding AWS Networking Costs: The Basics
Before diving into the tactics, it helps to understand how AWS charges for networking:
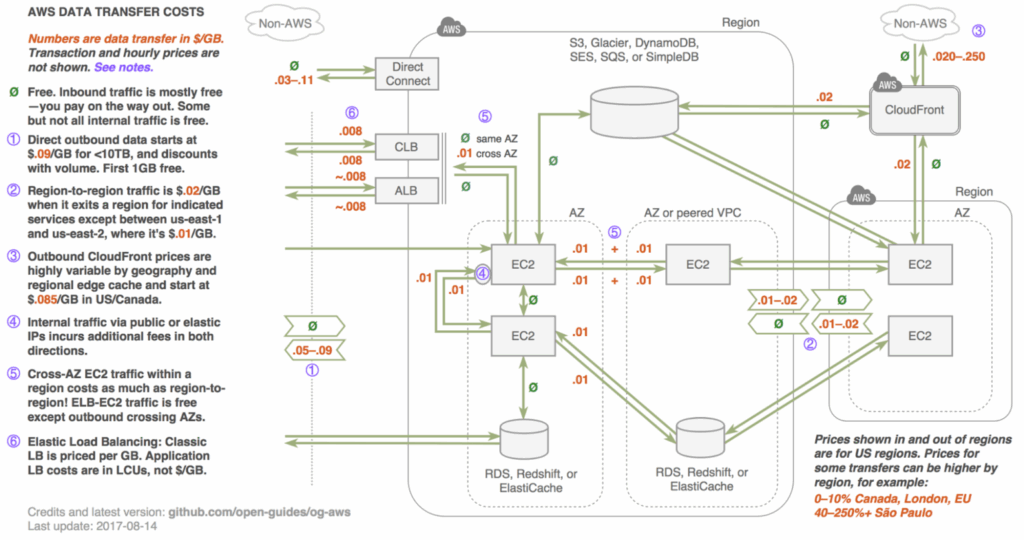
| Scenario | Cost Behavior |
|---|---|
| EC2 → EC2 in same AZ, private IP | Free |
| EC2 → EC2 in different AZs | $0.01/GB (intra-region data transfer) |
| EC2 → EC2 in different Regions | $0.02/GB (Inter-region data transfer) |
| EC2 → Internet via public IP | $0.09/GB (data transfer out to internet) |
| EC2 → S3 or other services | Varies, often incurs cross-service charges |
These charges can quietly accumulate, especially in high-throughput architectures or data-intensive pipelines.
💡Tip 1: Use Private IPs for Internal Communication
Using a public IP between AWS resources — even in the same region — routes traffic out through the internet gateway and back in. That incurs public data transfer charges.
Instead:
-
- Configure your EC2 instances, containers, or services (like RDS or ElastiCache) to use private IPs or DNS names resolving to private IPs.
-
- Place your resources in private subnets and use VPC peering or Transit Gateway when needed — both support private routing.
Savings: Avoid the $0.09/GB outbound charge when you don’t need public exposure.
Bonus: It also improves latency and security by keeping traffic within AWS’s private backbone.
💡 Tip 2: Deploy Services in the Same Availability Zone (AZ)
Even within the same VPC and region, cross-AZ traffic is not free. AWS charges $0.01/GB for data transferred between AZs.
Here’s how to optimize:
-
- Place tightly-coupled services (e.g., EC2 + RDS, EC2 + Elasticsearch) in the same AZ when high data exchange is expected.
-
- Use placement groups if needed to keep compute instances in close proximity.
-
- Be cautious with autoscaling and multi-AZ deployments — great for availability, but may increase cross-AZ traffic if not managed carefully.
Example: A microservice-based architecture with chatty inter-service communication can rack up significant intra-region fees when containers span multiple AZs.
📉 FinOps Wins: Simple Choices, Compounding Results
Let’s look at a quick cost example:
| Scenario | Data Transfer | Monthly Cost (at 10 TB) |
|---|---|---|
| EC2 to EC2 in same AZ, private IP | 10 TB | $0 |
| EC2 to EC2 across AZs | 10 TB | $100 |
| EC2 to Internet (public IP) | 10 TB | $900 |
That’s a 9× difference between private and public IP usage for the same amount of traffic.
🛠️ Implementation Checklist
-
- Use private DNS names or IPs for all internal traffic
-
- Configure VPCs to prioritize private subnets
-
- Audit services communicating across AZs
-
- Use placement groups or AZ-aware service discovery
-
- Educate dev teams: cross-AZ ≠ free
📊 Monitor and Visualize: Add It to Your FinOps Dashboard
Include networking cost metrics in tools like:
-
- Grafana (via Athena + CUR)
-
- Looker Studio (via BigQuery or GCS exports)
-
- AWS Cost Explorer → Use filters for “Data Transfer”
Track KPIs like:
-
- Cost per GB transferred
-
- Cross-AZ data transfer volume
-
- Public IP egress cost trends
🧭 Final Thoughts
AWS networking costs are predictable and avoidable — but only if you design with awareness. By defaulting to private IPs and same AZ placement, you can significantly reduce spend while improving speed and security.
This is low-hanging FinOps fruit that every team should pick.
📣 Call to Actons
Ready to make smarter networking choices? Start by analyzing your VPC flow logs and CUR data to identify public IP or cross-AZ patterns. Then, refactor deployments or automate placement strategies to optimize for cost and performance.